There is now a new exploit that has been uncovered in TouchWiz on the Samsung Galaxy S IIÂ and Galaxy S III. A single line of code that can penetrate your device will send the phone into a panic and factory reset the device over and over again. Reports suggest other Samsung TouchWiz based device could also be affected.
The hack is a simple USSD code. you know, the ones that you type in on your phones dialer to return your billing info, number of minutes and texts. The USSD code can be sent out from a website, triggered by NFC or a QR code scan that will rest your device. In a nut shell, this is bad.
Current solutions to the issue include turning off and deactivate any automatic site-loading in any QR and/or NFC reader software you have installed on your device. Don’t click on any links that you don’t trust and use a browser that isn’t the stock browser found pre-installed.
A few users and readers from TmoNews have related info that the Galaxy Nexus is exempt of course thanks to the stock Android experience. Also anyone that is rooted and sporting an AOSP based build of Android are also safe from the attack (CM10, AOKP ect.. ). Further, if you are running a stock install of the latest Jelly Bean leaks with TouchWiz, you are safe too.
Want to see what it does? Check out the video below.
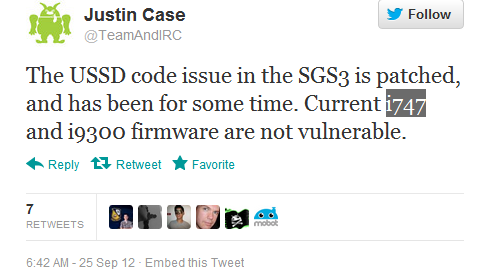
Update: So after pushing this out to our followers we got a lot of mixed responses. Some of that is easily our fault, but also the variety of devices on the market. Apparently there has been a patch issued that solves this problem. All current i747 SGS III’s, AT&T are fine. So are all International SGSIII’s, i9300. We are now working our way through the web to find out about T-Mobile’s T999 and Verizon’s version too. As soon as we find out more we will let you know here.