
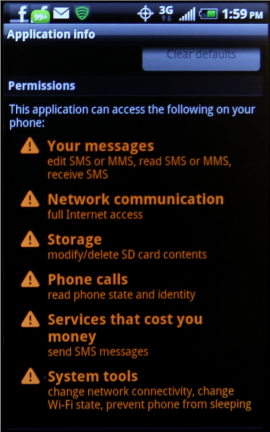
The FTC finally settled with HTC America regarding gaping security issues first found in late 2011 and addressed some newer concerns. Initially, some devices including, but not limited to the EVO 4G, EVO 3D, Sensation, EVO Shift 4G, MyTouch 4G Slide, and Thunderbolt could give an app access a huge amount of hidden permissions unbeknownst to the user simply by having an Internet permission. There were also concerns about Carrier IQ (CIQ) and HTC Loggers as well. The FTC also found that user manuals for all devices were deceptive since the Tell HTC error reporting app did not allow users to opt-out of user location even though there was an option for it. The Internet permission exploit is demonstrated below:
The FTC said it best:
“Among other things, the complaint alleged that HTC America failed to provide its engineering staff with adequate security training, failed to review or test the software on its mobile devices for potential security vulnerabilities, failed to follow well-known and commonly accepted secure coding practices, and failed to establish a process for receiving and addressing vulnerability reports from third parties.
To illustrate the consequences of these alleged failures, the FTC’s complaint details several vulnerabilities found on HTC’s devices, including the insecure implementation of two logging applications – Carrier IQ and HTC Loggers – as well as programming flaws that would allow third-party applications to bypass Android’s permission-based security model.
Due to these vulnerabilities, the FTC charged, millions of HTC devices compromised sensitive device functionality, potentially permitting malicious applications to send text messages, record audio, and even install additional malware onto a consumer’s device, all without the user’s knowledge or consent. The FTC alleged that malware placed on consumers’ devices without their permission could be used to record and transmit information entered into or stored on the device, including, for example, financial account numbers and related access codes or medical information such as text messages received from healthcare providers and calendar entries concerning doctor’s appointments. In addition, malicious applications could exploit the vulnerabilities on HTC devices to gain unauthorized access to a variety of other sensitive information, such as the user’s geolocation information and the contents of the user’s text messages.”
So what’s in the settlement?
- HTC is ordered to release patches within 30 days.
- HTC is required to provide a “comprehensive security program designed to address security risks during the development of HTC devices”.
- The FTC “prohibits HTC America from making any false or misleading statements about the security and privacy of consumers’ data on HTC devices”.
- HTCÂ WILL BE SUBJECT TO AN INDEPENDENT SECURITY REVIEW FOR THE NEXT 20 YEARS!
The initial issues found in 2011 were patched soon after with updates, but the 30 day patch order covers software on all devices dating back to December 2010. Hopefully this carpet bomb of required new patches for such old software will be a wake-up call to HTC for future software releases. Security and privacy concerns are a big deal and I’m glad the FTC is taking this seriously, since HTC surely wasn’t.
Source: Â Ars Technica
Find the full FTC complaint here the full FTC order here, and the FTC settlement summary here.









